Linux for Gamers: How to Run Games on Linux
How to Run Games on Linux. Linux has evolved from being a developer’s playground to a versatile operating system for various purposes, including gaming. If you’re a gamer curious about using Linux, you might be wondering: Can you run games…
Best Linux Desktop Environments for Productivity
Best Linux Desktop Environments. Linux offers a wide range of desktop environments tailored for different needs. Whether you’re a developer, a designer, or simply looking for a clean and organized workspace, the right desktop environment can significantly boost your productivity….
Introduction to Linux Shell Scripting
Linux shell scripting is a powerful way to automate tasks, manage systems, and simplify workflows. By writing scripts in a shell, users can execute a sequence of commands in one go, saving time and effort. Whether you are a beginner…
How to Optimize Linux Performance for Fast Computing
How to Optimize Linux Performance. Linux is a powerful and versatile operating system, but even the best systems need a little tuning to perform at their peak. How to Optimize Linux Performance. Whether you’re using Linux for personal computing or…
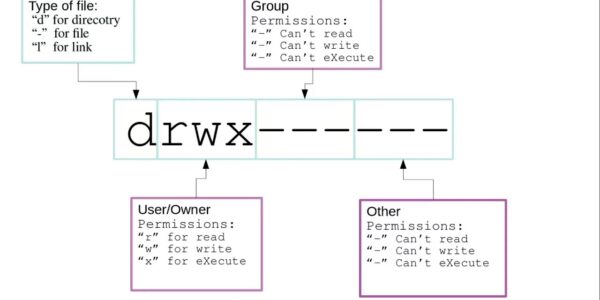
Understanding Linux Permissions: A Beginner’s Guide
Linux permissions are a fundamental part of managing files and directories in a Linux system. They ensure security and control by specifying who can read, write, or execute a file. Whether you’re a beginner or just need a refresher, this…
Top Linux Tools for Web Developers
Linux Tools for Web Developers. Linux is a powerhouse for web developers, offering tools that are fast, flexible, and often free. With its open-source nature, Linux provides developers with a customizable environment tailored to their needs. If you’re a web…
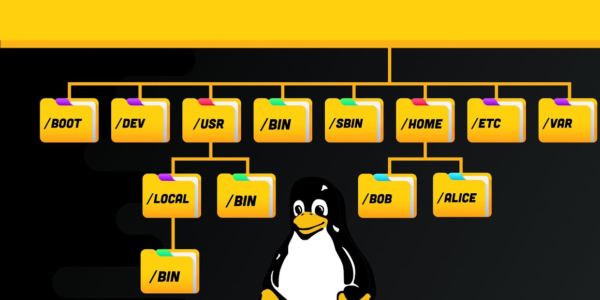
Linux File System Explained: Everything You Need to Know
Linux File System Explained may seem complex at first, especially if you’re coming from a Windows environment. However, understanding the Linux file system structure can empower you to navigate and manage files more efficiently. This guide breaks down everything you…
How to Install Linux on Any Device
How to Install Linux on Any Device. Linux is a powerful, open-source operating system that can be installed on almost any device, from desktop computers to laptops, tablets, and even some smartphones. With the right approach, you can install Linux…
10 Reasons Why Developers Prefer Linux
LWhy Developers Prefer Linux. Its flexibility, customization options, and power-packed features make it ideal for software development, system administration, and other technical fields. Why Developers Prefer Linux. But what exactly draws developers to Linux? In this article, we’ll explore the…
Linux vs. Windows: Which OS is Right for You?
Linux vs. Windows: Which OS is Right for You?.Choosing between Linux and Windows can be challenging. Explore the pros, cons, and unique features of each OS to find the one best suited to your needs.Linux vs. Windows.Choosing an operating system…